LTIMindtree’s Threat Deception Service
Hackers and attackers are getting smarter every day, by gaining intelligence afforded by advanced technologies. Targeted attacks are now designed to defeat & bypass traditional security solutions, and are difficult to manage if we stick to the conventional approach of strengthening the existing security solutions. Traditional approach leaves many questions unanswered, cannot always detect advanced targeted attacks, and is unable to track lateral movements. The threat intelligence it provides is also insufficient, and often leads to multiple false alarms. To overcome these challenges, an “active defense” is required, which can counter the attacker with similar intelligence, and gain control over his / her actions.
LTIMindtree’s Threat Deception Service implants virtual “pots of gold” across the network, enticing the stealthiest hackers into revealing themselves, and drawing them away from the real assets. It creates private threat intelligence “decoys” of seemingly real systems. These decoys deceptively engage with the attackers to absorb the attack traffic and thwart the attacks effectively.
Our Threat Monitoring & Hunting team at Cyber Defense Resiliency Center or CDRC captures the alert and initiates investigation immediately. This also helps in overall reduction in number of alerts and assists in enabling continuous response mechanism, without any performance impact on the production system. Our services are delivered in flexible deployment models, and do not cause any network performance impact, or create a risk of a downtime.
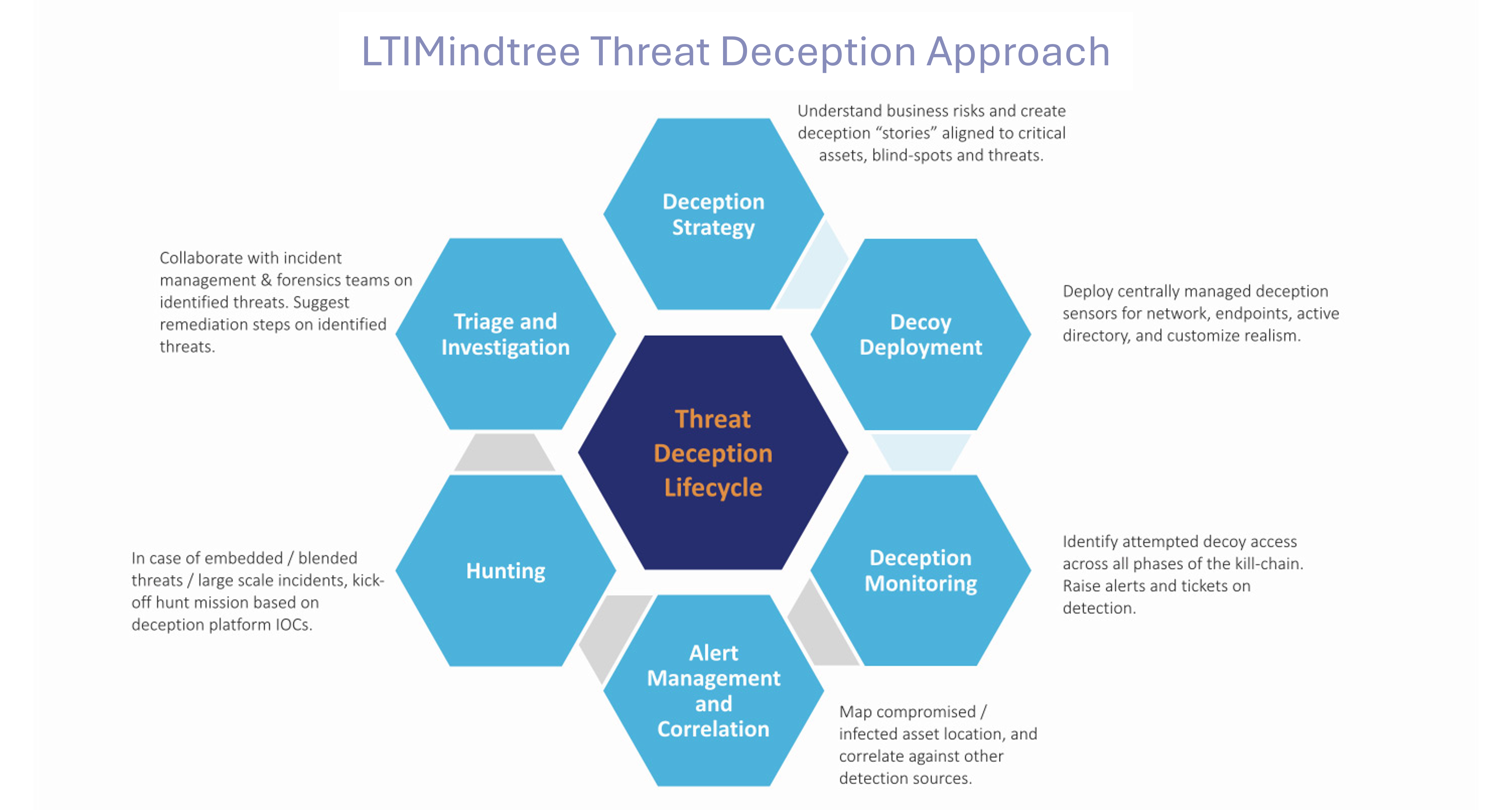
Key Highlights
- Deployment of decoys as UAT / testing, login portals, VPNs, endpoints, networks, etc.
- Real-time alert generation, by collecting and using attack telemetry.
- Integration of attack activity & alerts with SIEM and cyber analytics engines.
- Absorb and analyze zero-day exploits, including the brute force attacks.
Key Benefits
- Improved Threat Detection – Faster detection directly reduces incident costs.
- Higher Quality Alerts – Reduced cost of triaging alerts, improved security team productivity.
- Blind-Spot Reduction – Improved visibility into currently unmonitored areas, scales easily.
- Faster Detection Time – Reduced average time to detect and remediate threats.
- Low Friction Deployment – Quick and easy to implement, without any production impact.



