Top Strategies for Securing Hybrid and Multi-Cloud Environments
Today, enterprises prefer multi-cloud strategies as they can reap features of different cloud providers, making their infrastructure far more flexible and scalable. 98% of Indian enterprises using the public cloud have adopted multi-cloud infrastructures, platforms, and services to run their business1.
A multi-cloud environment allows enterprises greater flexibility compared to a single-cloud platform. It helps enterprises manage costs, avoid single-cloud provider lock-in, and improve the organization’s resiliency. However, due to the added complexity of the multi-cloud environment, it can potentially increase the attack surface and risks of cyberattacks. Therefore, businesses should consider addressing and preparing for multi-cloud security challenges before they begin their deployment and must develop a thorough and efficient multi-cloud security plan. This article will explore the security challenges in multi-cloud environments and how to mitigate them.
Security challenges with hybrid and multi-cloud environments
Enterprises using multiple cloud providers to host their crucial data and applications are faced with a new set of challenges. Here are some of the biggest challenges with hybrid and multi-cloud environments.
Lack of visibility into cloud resources
Due to a lack of visibility in the cloud resources, managing and proactively detecting misconfigurations and security risks in a multi-cloud environment is difficult. Organizations find it challenging to maintain visibility and control over their applications and implement effective security policies and controls.
Difficulty in integrating on-premises policies and updates
This is one of the main challenges in ensuring consistent security across different cloud platforms while adhering to existing on-premises policies. On-premises policies are typically designed to address specific security requirements and compliance standards that may not directly translate into the cloud environment.
Security posture management
Hybrid and multi-cloud environments compound this challenge, which decreases trust and increases apprehension. Maintaining a consistent and effective security posture becomes even more challenging in multi-cloud environments, where data and applications are distributed across various cloud service providers.
Audit preparation and compliance with the industry requirement
With multiple cloud providers involved, it becomes essential to have a comprehensive understanding of each provider’s security protocols and compliance requirements. This includes conducting thorough audits to assess the effectiveness of security controls and identify any potential vulnerabilities or non-compliance issues.
Unified Identity and Access Management (IAM) framework
In a multi-cloud environment, organizations use multiple cloud providers to meet their diverse business needs. Managing user identities and access across different platforms can be complex and challenging. A unified identity and access management framework can provide a centralized solution for managing user identities, access control, and authentication across all cloud platforms.
Encryption prioritization- As data is constantly transferred between on-prem to the cloud (data in rest and motion) in a multi-cloud environment, enterprises are concerned about ensuring the availability, integrity, and confidentiality of data. It can lead to data theft and alteration incidents without proper encryption.
Securing hybrid and multi-cloud with CSPM and CWP Strategies
We first identify the threats and security vulnerabilities affecting hybrid and multi-cloud workloads using Microsoft’s Defender for Cloud to strengthen the security of hybrid and multi-cloud environments. The cloud security suit features:
- Cloud security posture management (CSPM) – Microsoft Defender for Cloud is free to all Azure users. It includes CSPM features like secure score, detection of security misconfigurations in Azure machines, asset inventory, and many more. You can use CSPM features to strengthen hybrid and multi-cloud posture and track compliance with the built-in policies.
- Cloud workload protection (CWP) – Microsoft Defender for Cloud integrates the cloud workload protection platform (CWPP), providing advanced, intelligent, hybrid, and multi-cloud resources and workloads protection.
A multi-cloud security solution also includes the Azure Network Security capabilities, giving you an overview of selected Azure Network Security products. Moreover, Azure Arc secures the on-premises and workloads in other CSPs like AWS and GCP. Once Azure Arc is enabled, those non-azure resources become Azure resources, and Microsoft Defender for Cloud provides recommendations on vulnerabilities and threats.
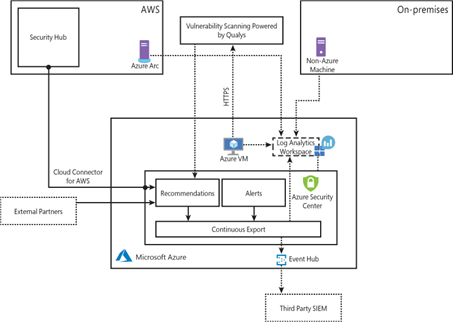
Figure 1: Connectivity between the Security Center and other services
The Microsoft Press Store, May 30, 2021: https://www.microsoftpressstore.com/articles/article.aspx?p=3113587&seqNum=2
Here are some of the key benefits –
- A better view of existing vulnerabilities and solutions to reduce the attack surface area for hybrid and multi-cloud workloads
- Prioritization and mitigation of potential threats found during the assessment and road map to fix the same
- Azure Network Security capabilities enhancement and appropriate usage to protect against threats
Conclusion
We are entering into the era of the hybrid and multi-cloud environment, and it has become important to be aware of the critical risks and challenges associated with it. The key to effective multi-cloud security is to have a sound security strategy and solution in place, which consists of the right approach, skilled resources, and efficient tools. With such a strategy, organizations can ensure the protection of their cloud workloads and maintain the security and integrity of their cloud environments.
References
- 98% of Indian Enterprises Using Public Cloud Have Adopted a Multicloud Infrastructure, Express Computer, March 15, 2023: https://www.expresscomputer.in/cloud/98-of-indian-enterprises-using-public-cloud-have-adopted-a-multicloud-infrastructure-provider-strategy/95660/
Latest Blogs
The energy and anticipation were evident even before entering the arena, and attendees had…
A tectonic shift in wealth is underway, and agility is the key factor that will distinguish…
Educational institutions are at a crossroads where their future hinges on a single question:…
In times of market unpredictability, alternative investments offer a valuable advantage by…




