Securing Your Business Through The Lens Of Data Protection
In this growing interconnected world and breadth of services offered to consumers, it’s evident that businesses need to collect, process, and exchange relevant data with their consumers, partners, government agencies, and regulators.
With unlimited data generated by individuals, machines, organizations, states, and interconnected systems, there is a growing need to constantly gain clarity and rethink the means to secure business enterprises and, more so today, individual privacy and protect one’s own identity and data.
Is it vital to protect the data (Data Protection) or secure it (Data Security)?
Well, it is simple. We need to do both! While it sounds similar and interchangeably referred to convey the intent to secure data, it is distinct and entails independent technology solutions, processes, governance, and outcomes.
Data Protection essentially focuses on archiving and safeguarding your data against potential data loss or data corruption scenarios.
Data security helps protect your data from unauthorized access, which can lead to data extraction and extortion resulting in significant business impact.
In today’s large enterprises & SMEs, it is inevitable to have both strategies to build trust in the business ecosystem. Consider a situation wherein your Data Security fails to guard your crown jewel (data); then, well-executed data protection will facilitate the recovery of your clean copies.
Data protection is paramount to sustaining and thriving businesses.
In this article, I want to bring forth some of the key pointers to consider regarding data protection while not discounting that data security and protection are both sides of the same coin.
When businesses converge to bring compelling services and efficient operating models and technology transforms the cloud and edge, it becomes imperative to rethink the data protection strategy.
- Protect your data and critical systems
Quite simply, it is super important to invest in the right technology stack to protect your data and have the ability to recover faster and easier. There is no shortcut.
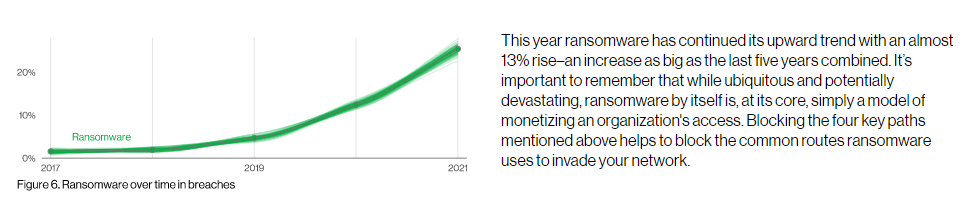
Source: Verizon Databreach Investigations Report 2022
With persisting challenges like ransomware, malware, phishing attacks, supply chain, and the human element, protecting your critical data is key to being in business.
60 Percent of Small Companies Close Within 6 Months Of Being Hacked
- Converge to solve, protect, and operate
Protecting business in today’s interconnected industry is a partnership with the CIO and CISO to bring value and benefit from this synergy. And it is best done with ‘data’ at the core and identifying best-fit solutions that extend the capability to protect the data and integrate with the security technology and operations. Collaboration and integration are paramount with emerging CDO (Chief Data Officer) roles.
- Continuous collaboration, validation, and vigilance
With evolving as-a-Service offerings and infrastructure as a ‘code,’ the days are bygone when teams can contest accountability for security response and recovery. Data protection solutions bring together the teams to reinforce the need to collaborate, jointly validate the approaches, and extract value from investments. Data and Security operations must collaborate, increasing telemetry captured across the enterprise and reducing operational complexity.
- Proactively govern, collaborate, and control.
Data protection should be by design and diligently planned by default. These are some principles included in the General Data Protection and Regulation (GDPR). With most states reinforcing that any breach needs to notify authorities within 45 days or earlier, it forces the business to consider redesigning the systems, processes, and services to protect personal data.
- Consistent and reliable operations
Bringing together the various functions and cohesively organizing the systems and processes while eliminating hurdles to protect the association is no easy task. It is best done using the right platform to automate processes and establish coherent data protection operations.
Protecting your enterprise with LTIMindtree VAULT
The LTIMINDTREE VAULT enables you to shift from your traditional methods for data recovery to a modern, fast, reliable data protection strategy and solution. LTIMINDTREE’s in-depth expertise in advisory and managed services and Rubrik’s zero-trust data protection platform provides you with a complete cyber-recovery solution. This service includes an assessment, discovery, and migration with ongoing management services by backup and ransomware experts.
An integrated solution with LTIMindtree VAULT, LTIMindtree CloudKnit, and MSOC (LTIMindtree NextGen Cyber Operations) brings together the cohesive function across Cloud, Data, and Cybersecurity delivery capabilities to address your overall business protection needs.
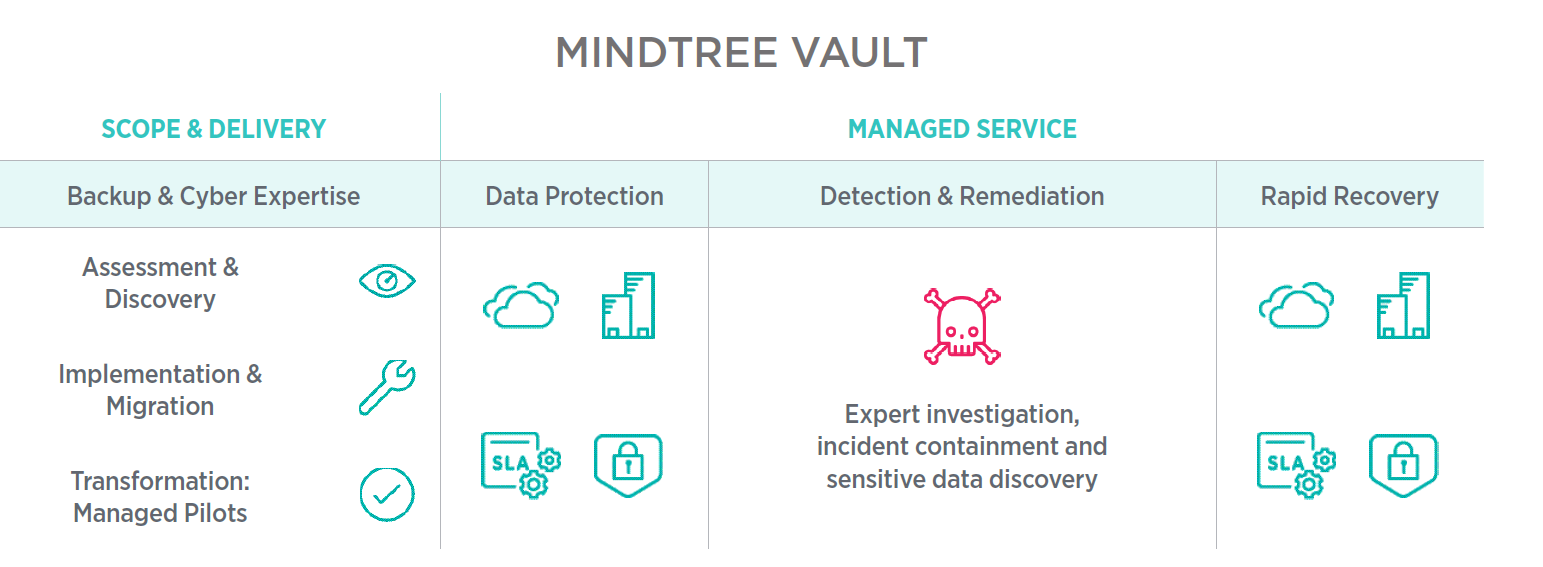
Integrated capabilities with Microsoft Azure and LTIMindtree VAULT
The rapid adoption of the Cloud-first strategy and the widely used Microsoft Azure platforms, including Microsoft Office 365, has compelled organizations to consider defense in depth from the edge to enterprise. Our integrated solution and deployment expertise bring together these capabilities for multiple benefits.
- Replicate your on-prem apps and data to Azure. Developers can quickly create apps in Azure for application recovery, testing, or development. Backup and recovery for Azure VMs, Azure NetApp Files (ANF), and Microsoft 365 applications can also be modernized with cloud-native protection and automated lifecycle management
- Virtual machines can also be flexibly recovered on-demand in Azure Virtual Machines in case of potential data center contingencies. Enable self-service for application test/dev cloud sandboxes.
- Safeguard your organization in the event of data loss, accidental deletions, and ransomware attacks with policy-based, fast, intuitive search and restore operations for Exchange Online, OneDrive, SharePoint, and Teams.
- Enterprise data estates can be cost effectively archived in Azure for secure, durable, long-term retention while having immediate data access with real-time predictive search.
Conclusion
We have observed an emerging trend of convergence of technology, data, and business driven by market needs and the exponential growth of cyber challenges. LTIMindtree can help you better address them, considering the pros (Protect and Proactive) and cons (Converge, Continuous, and Consistent) best suited for your unique environment and business priorities.
With the increasing amount of information we generate, process, and store, secure data equals trust in your business to grow and thrive.
More from Vijay Raghunaathan
Our global community has tackled multi-faceted threats to humanity over many centuries and…
Latest Blogs
Introduction What if training powerful AI models didn’t have to be slow, expensive, or data-hungry?…
Pharmaceutical marketing has evolved significantly with digital platforms, but strict regulations…
Leveraging the right cloud technology with appropriate strategies can lead to significant cost…
Introduction The financial industry drives the global economy, but its exposure to risks has…




