Securing Sensitive Data in a SaaS Ecosystem
Introduction to SaaS security
With the increasing adoption of cloud computing, businesses are turning to Software-as-a-Service (SaaS) solutions to streamline their operations and improve efficiency. Oracle, a leading provider of cloud services, offers a range of SaaS applications like Finance ERP, that are not only robust and feature-rich, but also prioritize security. In this blog, we will explore the various security measures and best practices to be implemented to secure SaaS applications on the cloud – From creating a secure access path to deployment and management to using innovative security measures like Oracle Break Glass.
The importance of prioritizing SaaS security
As more businesses adopt SaaS applications, it becomes crucial to prioritize security to safeguard sensitive data. While organizations may have experience securing Infrastructure-as-a-Service (IaaS) and Platform-as-a-Service (PaaS) environments, securing SaaS applications present new challenges:
- Complexity- SaaS applications serve multiple teams within an organization, leading to a high volume of usage and complexity. Different end-users with varying levels of technical knowledge access these applications, making it difficult for security teams to understand and manage the associated risks.
- Role of customer security team- Security teams often have limited interactions with business administrators who select and manage SaaS technologies. This lack of communication makes it challenging for security teams to understand the scope of use and potential threats posed by these applications.
- Collaboration- Internal teams supporting SaaS applications often prioritize functionality and business requirements over security. Balancing business needs with security requires constant collaboration. Organizations must allocate resources to identify and address security risks associated with SaaS applications.
Key security challenges associated with securing SaaS applications
Securing SaaS applications has its own set of unique security challenges, which must be addressed to ensure that the integrity and confidentiality of the data is not compromised. Below are a few key challenges while building a secure SaaS deployment:
- Regulating and auditing operations of the cloud service provider
- Evolving environments and user access
- Network security
- Fragmented platforms and applications
- Access controls and auditing
- Data security
- Secure management
- Infrastructure security
- Access control and auditing
Best practices to secure SaaS applications
To mitigate the forementioned security risks, building a layered security process is the best practice. Here are several key security practices to consider.
Secured and unsecured deployment for SaaS
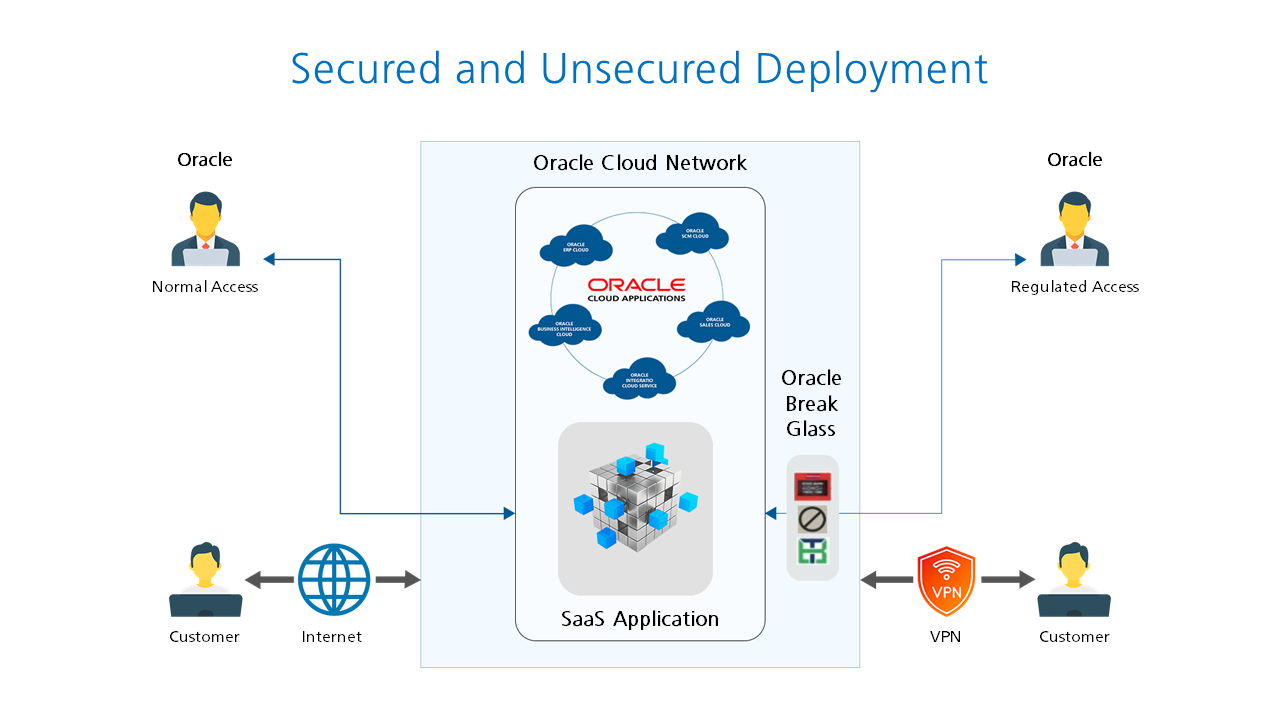
Providing access to a SaaS environment with a secure VPN/FastConnect path eliminates the risk of data flow over the internet. Second, using Oracle Break Glass, one can regulate the access to the Oracle application that manages the SaaS deployment. Besides regulation, it provides secure management by auditing the operations.
Building a layered security system
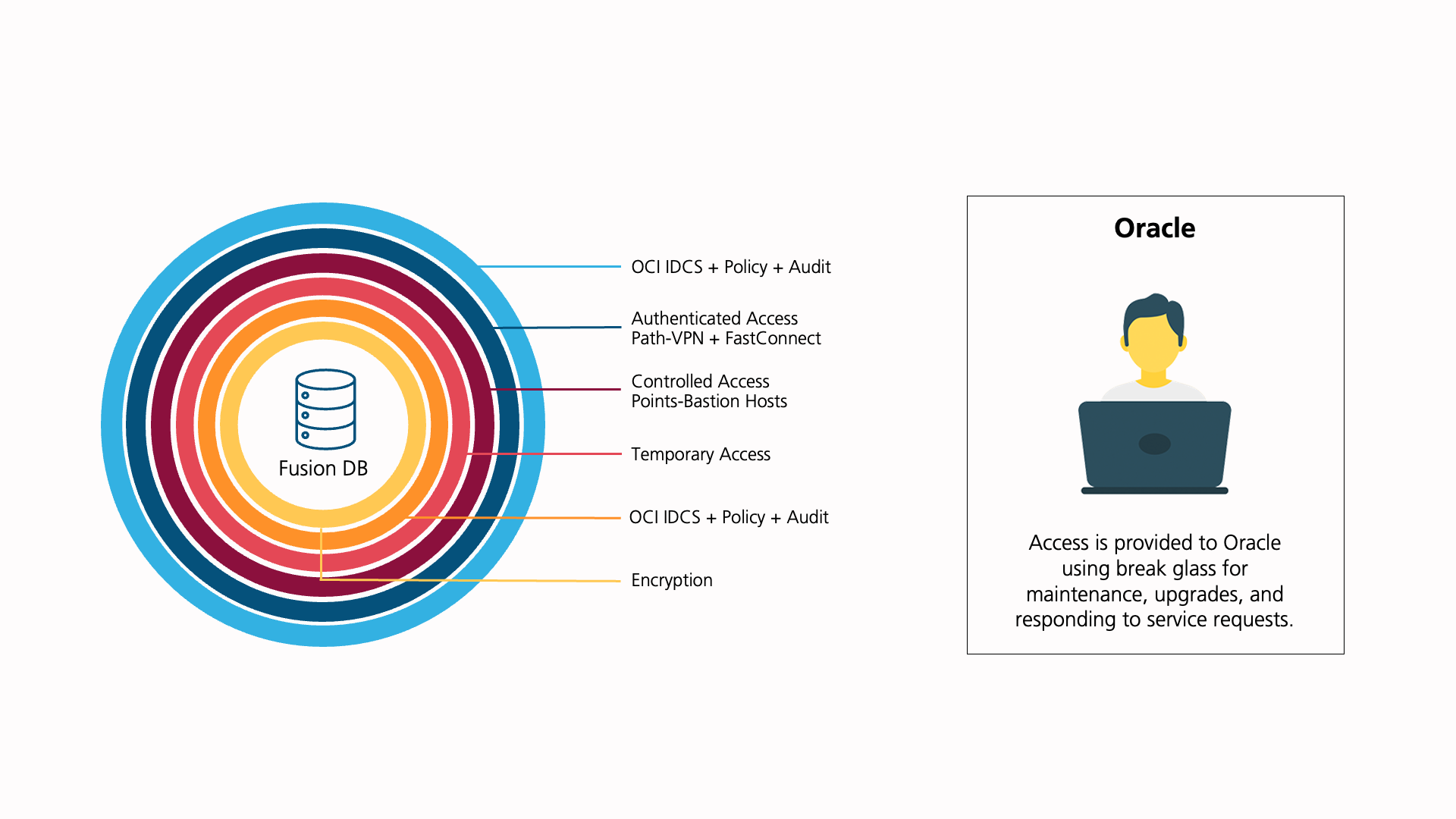
Layered security comprises Break Glass for controlled access to Oracle, in addition to ensuring the FastConnect path for end users to access applications.
Bring Your Own Key (BYOK) provides an extra layer of security by allowing companies to manage their encryption keys. This feature ensures that data remains encrypted and secure even if the cloud provider is breached. With BYOK, your encryption keys are stored by you, meaning only you can decrypt the data, even if the cloud provider has access to it. By taking control of your cryptographic keys using BYOK, you eliminate the risk of unauthorized third-party access to your data.
Finally, Fast Connect and IDCS are other security measures used in securing Oracle SaaS Finance ERP. Fast Connect provides a private connection to Oracle Cloud infrastructure (OCI) for enhanced security and reduced latency. By using Fast Connect, companies can securely connect to their SaaS applications and keep data safe, protected, and available always.
Conclusion
Securing SaaS applications on the cloud is a critical aspect of protecting sensitive data and maintaining the trust of customers. By implementing best practices, such as enhanced authentication, data encryption, Break Glass, and oversight, organizations can mitigate the security risks associated with SaaS applications. As technology advances, organizations must stay updated with emerging trends and adapt their security strategies to ensure the ongoing protection of their SaaS environments.
Latest Blogs
A closer look at Kimi K2 Thinking, an open agentic model that pushes autonomy, security, and…
We live in an era where data drives every strategic shift, fuels every decision, and informs…
The Evolution of Third-Party Risk: When Trust Meets Technology Not long ago, third-party risk…
Today, media and entertainment are changing quickly. The combination of artificial intelligence,…




