Implementing NIST-based Security Using AWS Native Services
Abstract
Cybersecurity is one of the biggest concerns in the digital era. Each enterprise is struggling with the fear of cyber-attacks and want to safeguard their data and infrastructure. While there are frameworks that safeguard data, a complete lifecycle of safety aspects like infrastructure, for instance, is not covered. Also, if any attack does happen, recovering and coming back the previous ‘safe’ stage is a challenge for all enterprise customers.
The most common concerns and questions raised by enterprises are about public cloud security compliance and governance. The top management often want to know about the comparison between on-prem and public cloud security and protection. They also sometimes ask about various security standards followed in the cloud, like the National Institute of Standards and Technology (NIST), Health Insurance Portability and Accountability Act of 1996 (HIPAA) etc., as these are pivotal for their industry.
This document provides guidelines and recommendations to manage cloud security and privacy on AWS cloud environments as enforced by NIST.
Overview of NIST
There are various international organizations working on different frameworks to streamline the cyber security framework (CSF), including NIST. The US federal government strictly follows the NIST framework. According to AWS, 30% of non-government organizations in the US are following NIST-based security frameworks.
NIST is based on five functions.
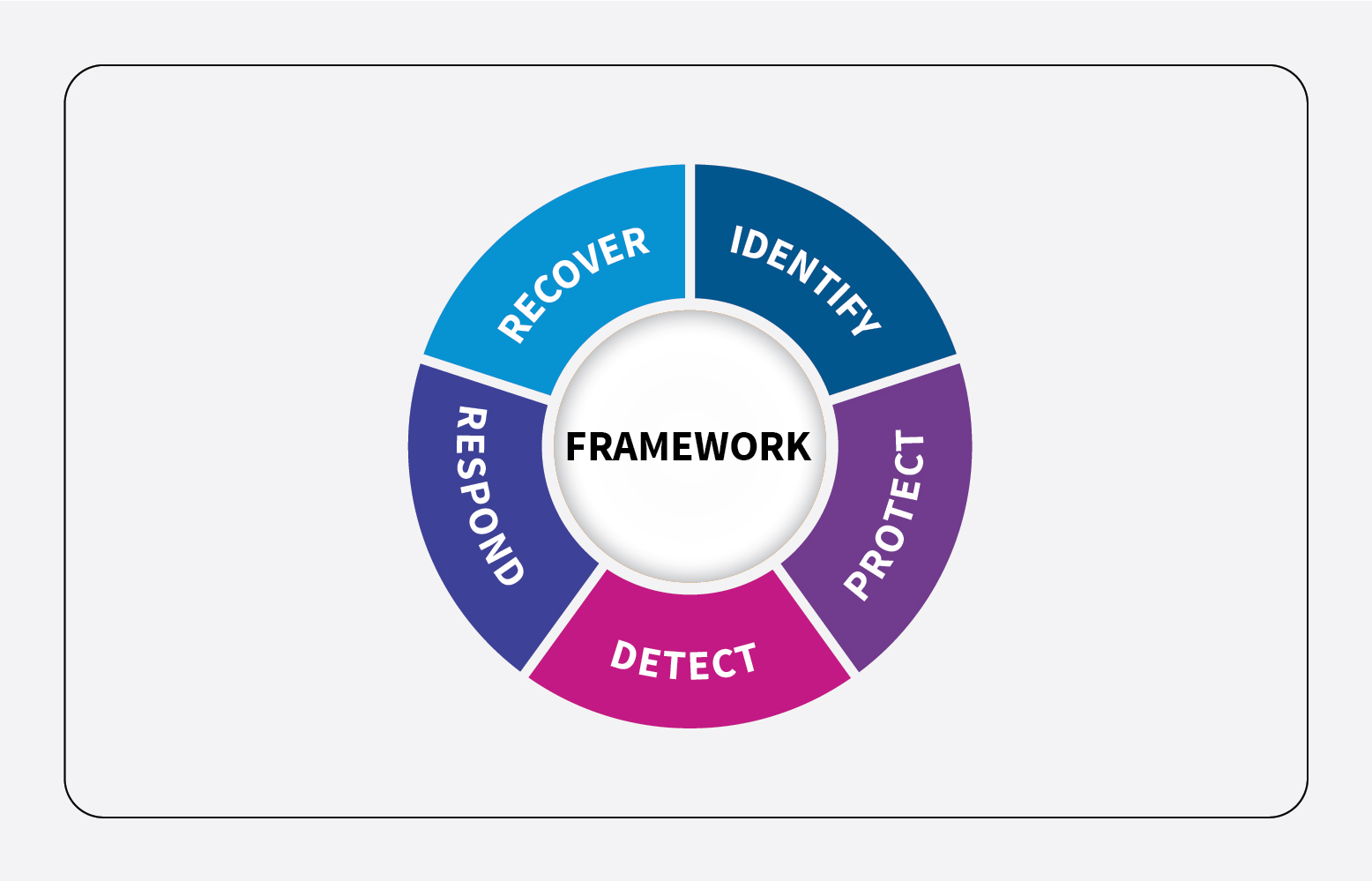
- Identify: NIST defines Identify as “developing organizational understanding to manage cybersecurity risk to systems, assets, data, and capabilities.” NIST focuses on the business and cybersecurity challenges to overcome.
- Protect: NIST defines Protect as “one of the key functions in managing an organization’s sensitive data.” It defines how organizations are managing and protecting information and implementing the right service to safeguard data.
- Detect: Three areas that cover the Detect function – continuous security monitoring, detection of threats, and keeping track of anomalies.
- Respond: One of the most important tasks is to inform the stakeholder in case of any events.
- Recover: Planning, continuous improvement, and communication to the respective stakeholders are major tasks during any pre attack or in case of any downtime.
Becoming NIST-compliant using AWS services
Today, many enterprises establish a security foundation with cloud-native services.
The AWS security model works on shared responsibility, translating to “Security of the Cloud” and “Security in the Cloud.” The below structure explains this security model with respect to the responsibility of the customer and AWS.
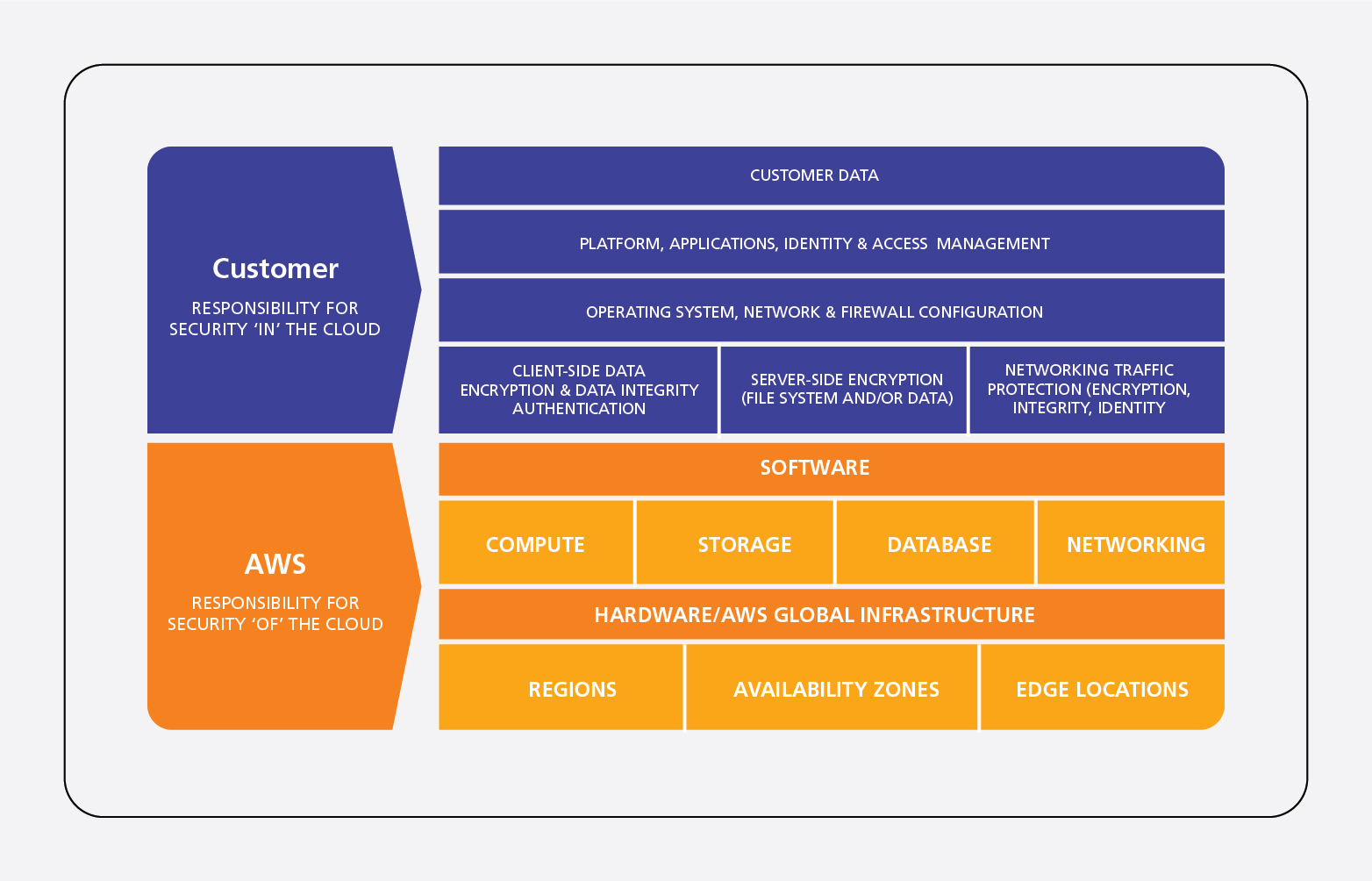
NIST with AWS best practices and CAF
AWS Cloud Adoption Frameworks (CAF) uses six pillars – business, people, governance, platform, security, and operations, to support customers’ AWS cloud adoption and ensure readiness for security. In parallel, the AWS well-architected framework helps customer implement NIST-based CSF. As a result, thousands of organizations are migrating their critical applications to the AWS cloud.
Function-wise NIST implementation on AWS
Identify:
Below are a few AWS native services that can be enabled on AWS environments to achieve the Identify function on NIST CSF.
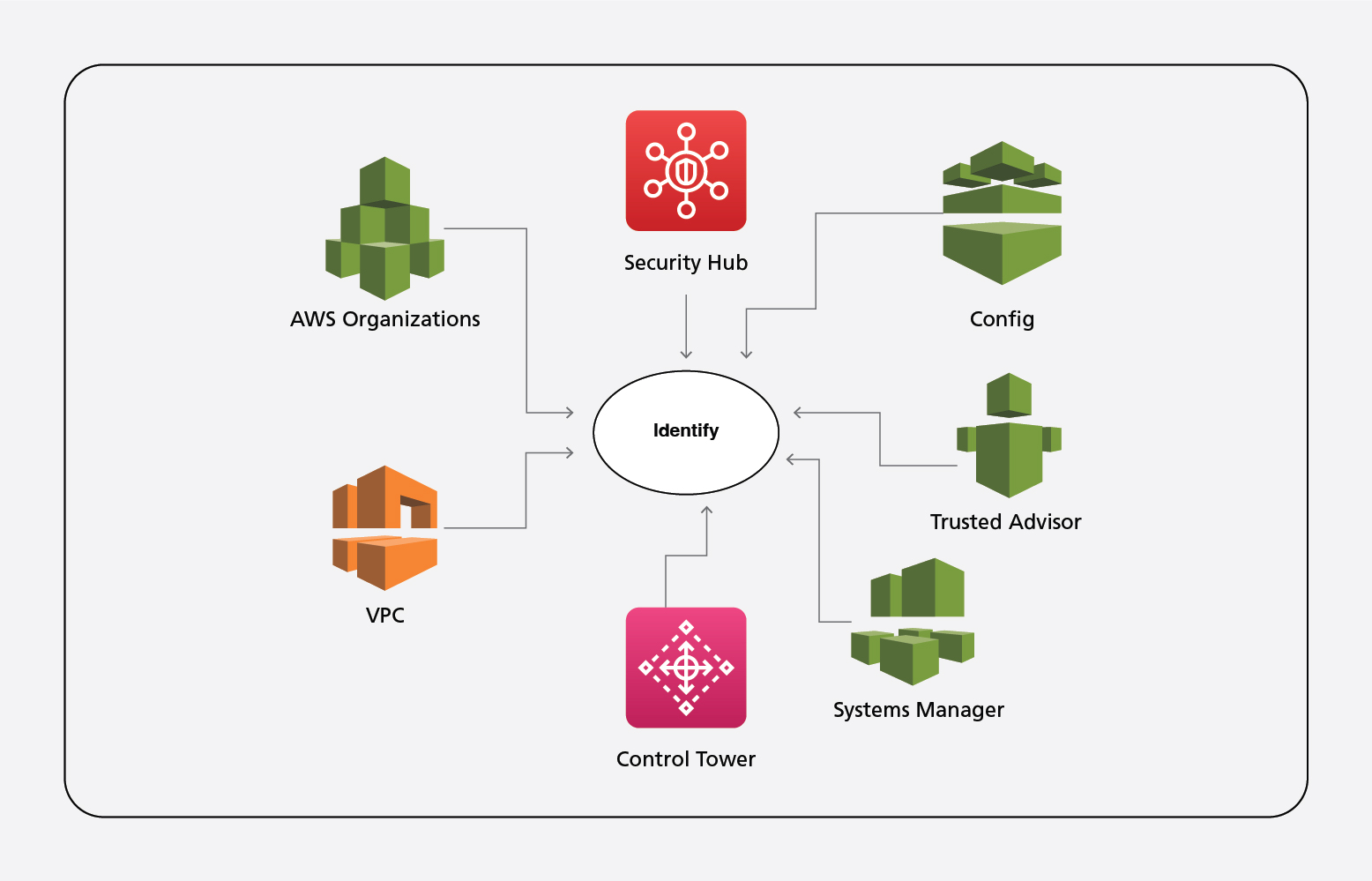
AWS Organizations help quickly scale AWS accounts with centrally implemented security features like user permission and governance management. It also helps maintain a central audit environment for all child accounts.
AWS Security Hub automates security and alerts on any security incident. It follows AWS Best Security practices and accelerates automated response remediation action centrally.
AWS Config continuously logs and monitors resources. It also follows the organization compliance policy and evaluates and audits the same.
Trusted Advisor implements security best practices and scans AWS environments to detect security leakages or vulnerabilities.
System Manager allows grouping of resources according to application management. It also gives control and visibility of the infrastructure.
Control Tower is the the easiest way to set up and govern a secure multi-account AWS environment.
Protect:
Below are a few AWS native services that can be enabled on AWS environments to achieve the Protect function on NIST CSF.
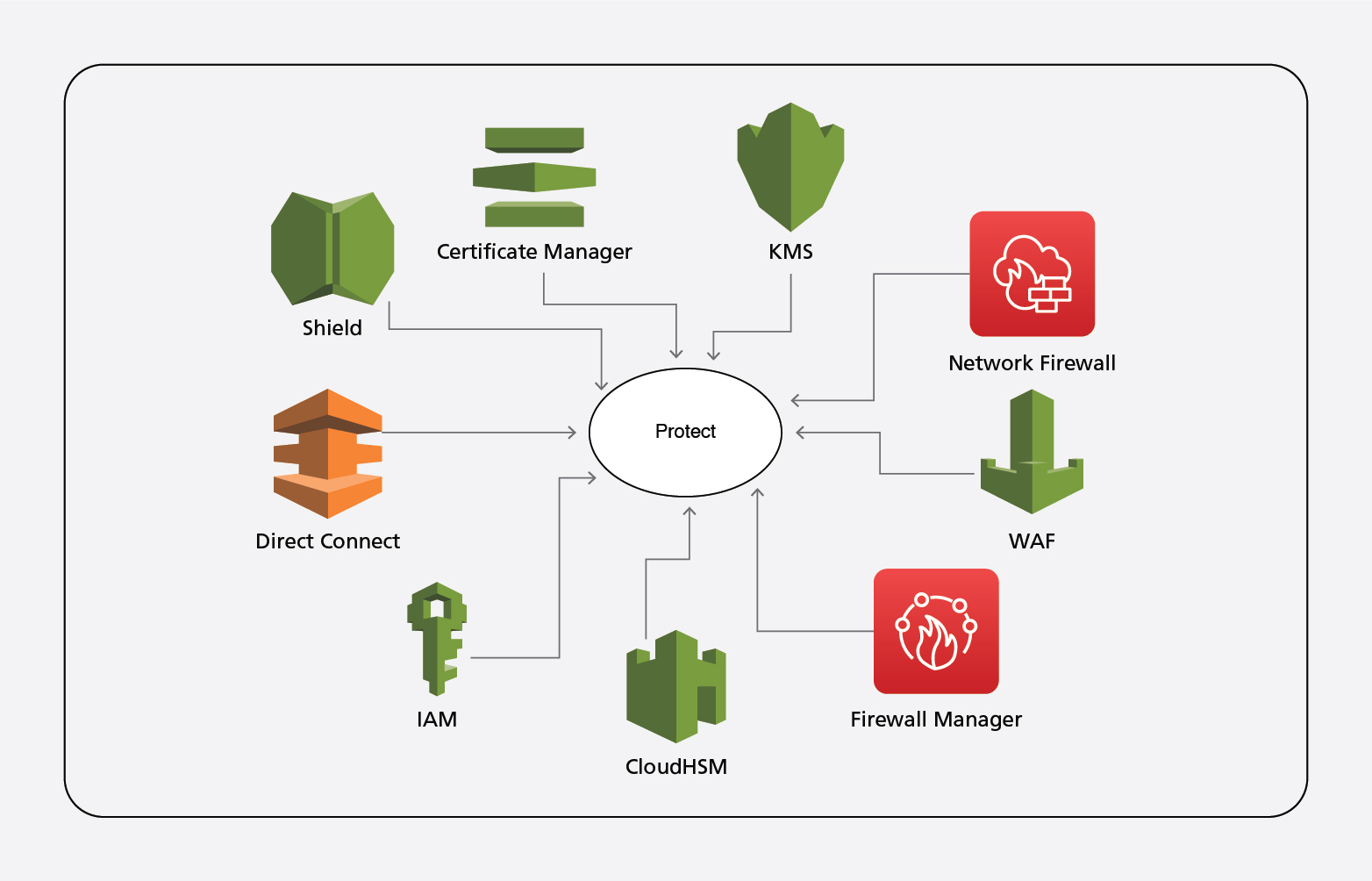
Certificate Manager centrally manages SSL/TLS certificates provided by AWS. It is designed to protect and manage the private keys used with SSL/TLS certificates.
KMS centrally manages all the keys and policies in just a few clicks. As this is an AWS managed service, there is no need for setup or maintenance.
Network Firewall manages and protects the network traffic with one’s own rules. It works together with AWS Firewall Manager and creates rules that are applied across Virtual Private Cloud (VPC). The Network Firewall can check and control outbound traffic, apart from protecting the VPN and direct connect, which are attached to the on-premises network.
WAF protects applications against threats by monitoring the http and https traffic and blocks any kind of common attack pattern, SQL Injection, bot traffic etc. As it’s an AWS managed service, AWS provides multiple predefined rules that just need to be activated.
Firewall Manager helps manage firewall rules across the AWS account. One can also manage preconfigured WAF rules across the account.
IAM – Identities and Access Management is one of the important functionalities of any IT infrastructure environment. AWS suggests the rule of least privilege, which can be managed through IAM.
Detect:
Below are few AWS native services that can be enabled on AWS environments to achieve the Detect pillar on NIST CSF.
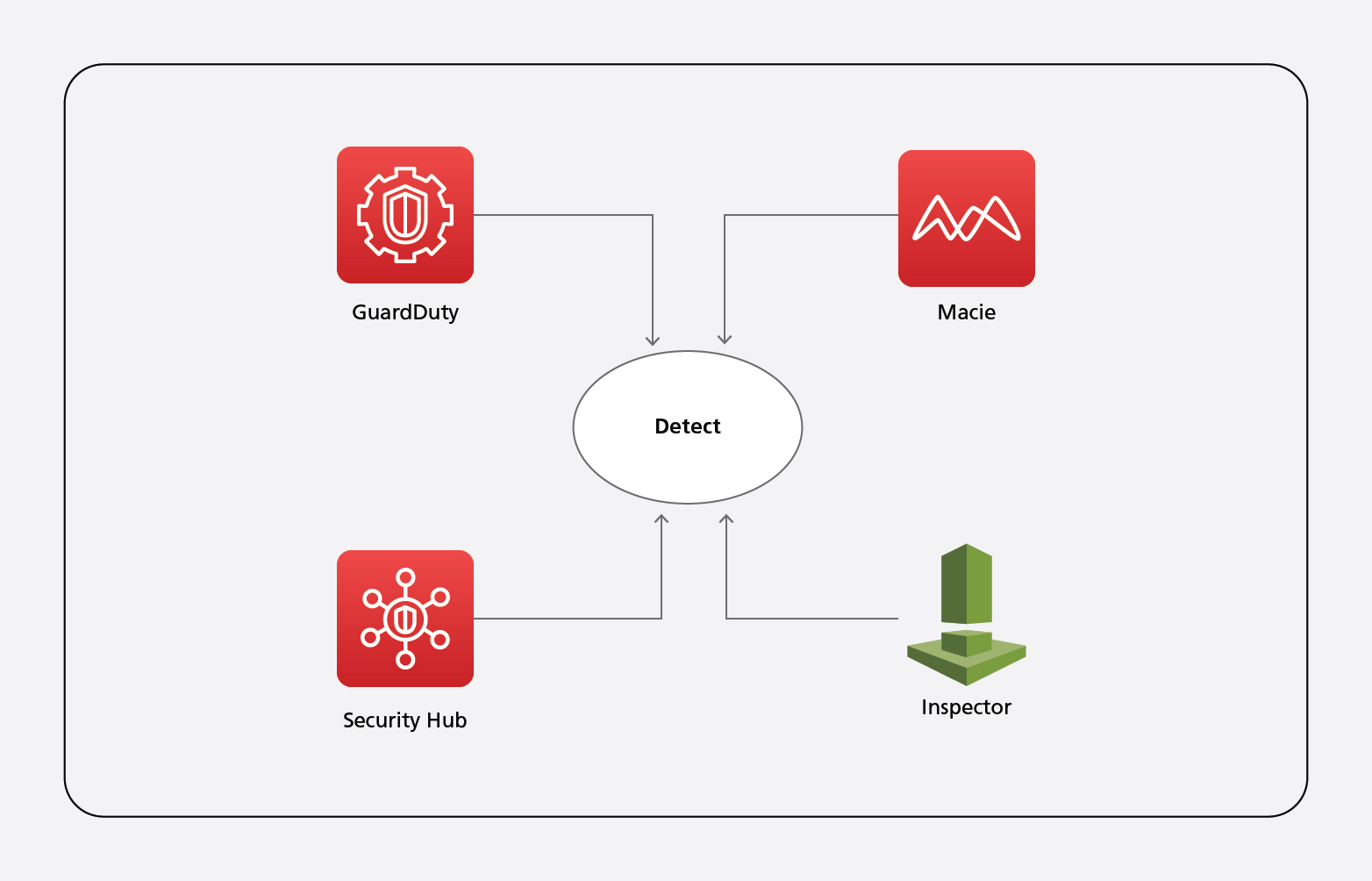
AWS GuardDuty is an advanced service that can be leveraged to proactively monitor the AWS account, EC2, containers, storage, user etc. Using machine learning (ML) and thread intelligence feeds, AWS GuardDuty mitigates threats early by initiating automated response.
Amazon Macie is a data security and privacy service that uses ML and pattern matching to discover and protect sensitive data. It automatically recognizes sensitive data at scale, stored in the EBS or S3. Also, it provides alerts on publicly accessing S3, unencrypting S3 etc.
AWS Security Hub automates security and alerts in case of any security incident. It follows AWS Best Security practices and accelerates the automated response remediation action.
AWS Inspector ensures automated and continual vulnerability management at scale. With AWS Inspector and EventBridge, one can reduce the Mean Time To Remediate (MTTR). It quickly discovers vulnerabilities and alerts the team for quick action.
Respond:
Below are a few AWS native services that can be enabled on AWS environments to achieve the Respond pillar on NIST CSF.
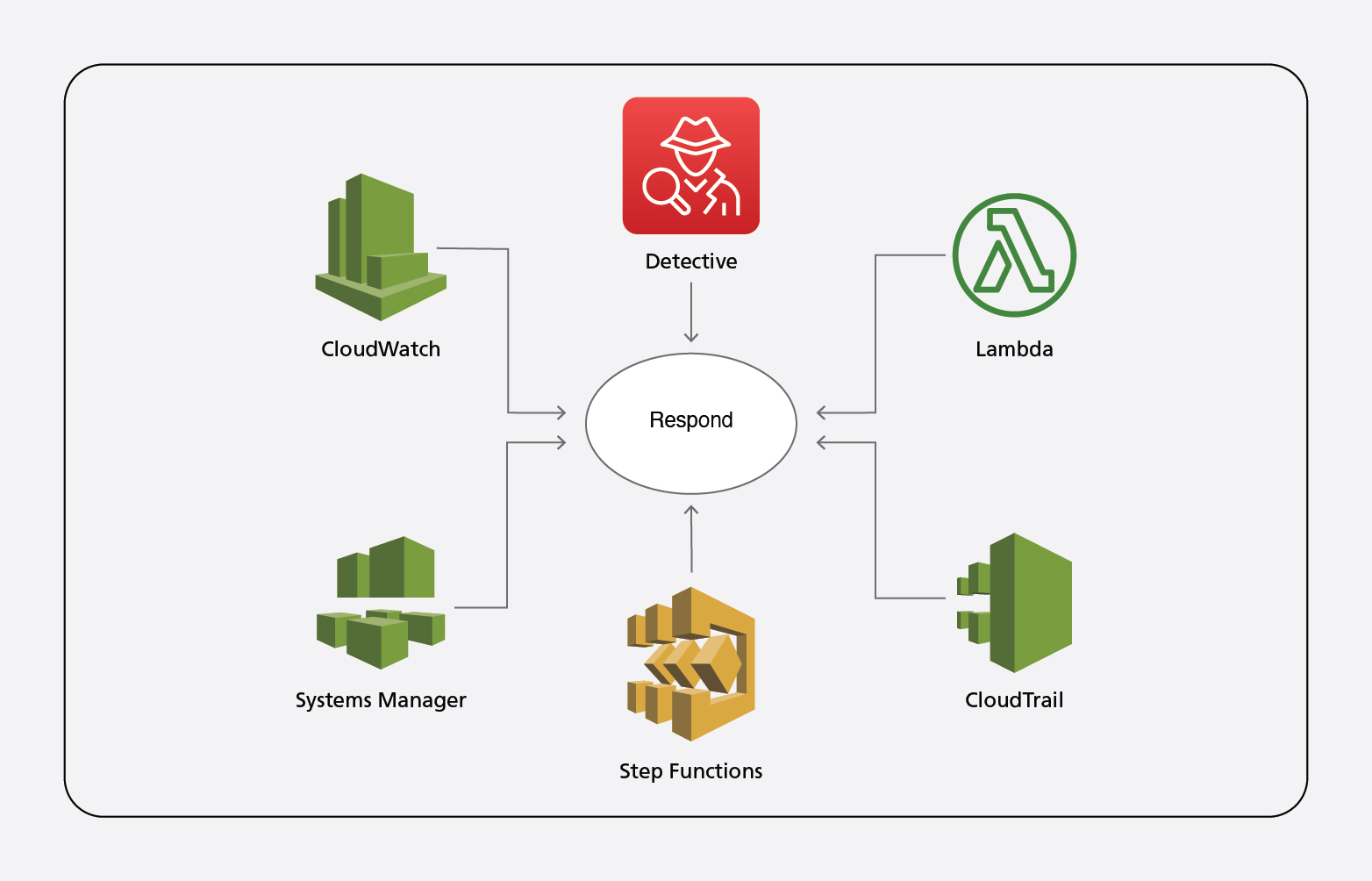
CloudWatch provides monitoring services of AWS resources like EC2, RDS etc. A user can enable real-time monitoring of AWS services. On top of that, one can enable any kind of trigger or call any Lambda function to initiate automatic fixes.
Detective analyzes and visualizes security data to investigate potential security issues. One can setup AWS Detective in an organization so that it applies to all child accounts.
Lambda – This is a service of AWS that helps run code without a server. One needn’t manage the infrastructure – and all that’s needed is for the code to be uploaded and run. Event-driven flow with scheduler can be used to achieve many automated response patterns. Response pattern could be a simple to execute single AWS Lambda function, or complex series of AWS Step Function tasks.
CloudTrail – AWS calls API when a user is carrying out an activity, and these records can be stored on CloudTrail. This helps find the RCA or any kind of audit activity.
Recover:
Below are a few AWS native services that can be enabled on AWS environments to achieve the Recover pillar on NIST CSF.
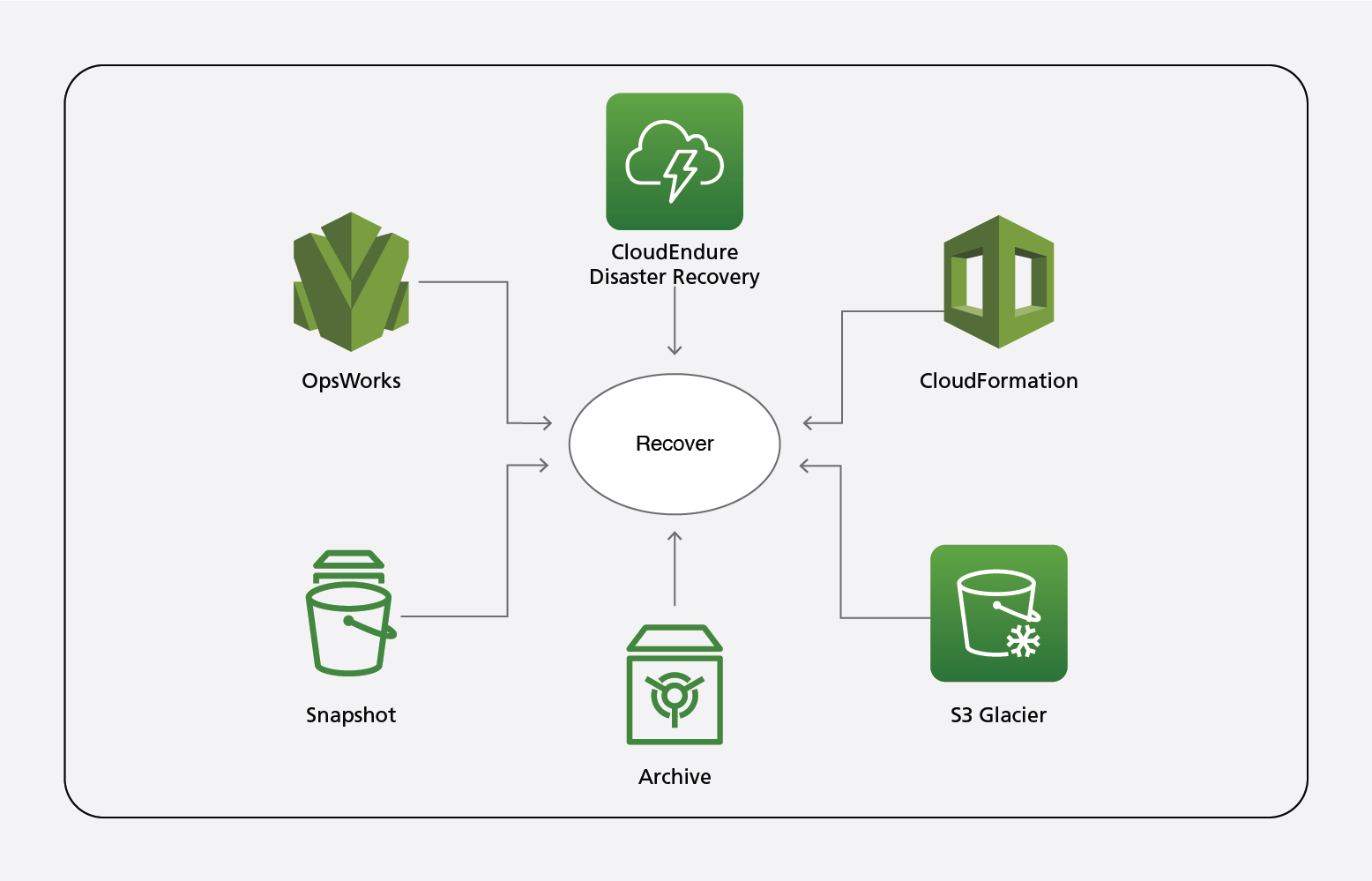
OpsWorks provides the facility to configure chef and puppet, which helps automate the configuration of the server. Also, it helps deploy and manage EC2 instances and on-prem VMs.
DRS (Cloud Endure) is a flexible disaster recovery service that can help recover the environment quickly in case of a disaster.
CloudFormation is an Infrastructure-as-a-Code (IaaS) service to help provision the environment quickly, apart from launching the VMs or DB rapidly.
S3 is AWS’s object storage that can store any amount of data with minimum costs. Apart from ensuring 11 9s durability, S3 has various options to store the data depending on the access frequency.
Bringing them all together
AWS has received third-party certifications for public and government cloud in the US, with respect to NIST’s standard infrastructure compliant setup. This means that all AWS infrastructure is NIST standard-compliant. However, all applications hosted on AWS are not its responsibilities, and hence, customers need to take care of application security.
Shown below is a suggested reference architecture that can be used to setup a NIS-compliant security setup, including applications.
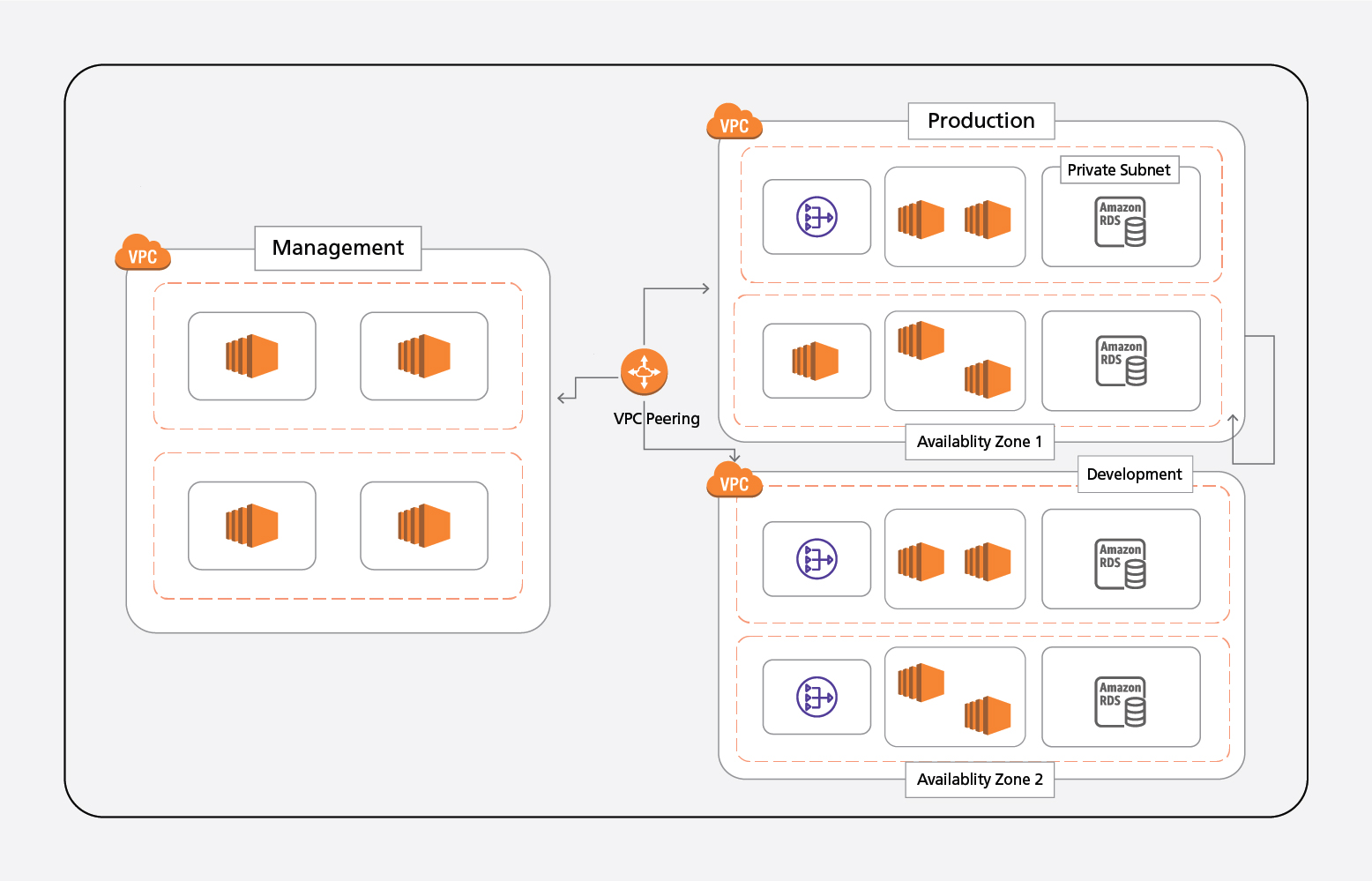
In the reference architecture, we have three VPCs, as below:
- Management: The Management VPC is used to control complete environments, such as security, monitoring, various logs (application, system, etc.).
- Development/Test/UAT: This is used for development/test/User Acceptance Testing (UAT). We may create different VPCs or accounts for these as well. However, in the reference architecture, these are shown as different VPCs. Before the application moves to the production environment, this is where testing should be done, and if required, then UAT as well. One needs to ensure that all security and validations are in place.
- Production: Used to host business application for the end user.
VPC peering is used to connect the three VPCs, along with access lists, and segmented network traffic and permissions. Inside every VPC, all the services are deployed in two different availability zones, for redundancy and fault tolerance.
Suggested best practices
Account Management
From an account management perspective, a few rules are suggested to follow AWS’ best practices.
- All the users should have strong password.
- Apply password rotation policy.
- Create a group and rule of least privileges, where all users should associate with a group.
- Enforce two-factor authentication.
- API key should be rotated on regular basis.
Continuous Monitoring
To continuously monitor the AWS environment, the below points can be considered.
- Enable CloudTrail.
- Maintain all logs and create log retention and lifecycle policy.
- Create CloudWatch for the application monitor.
Conclusion
This document attempts to provide a brief overview on how NIST-compliant secure setups can be achieved with native AWS functions without third-party tools. However, the architecture should be thoroughly checked by a seasoned AWS expert to ensure that cost and effectiveness are set up in a balanced manner.
AWS and LTIMindtree are helping customers embark on their cloud journeys and implement NIST-based security. To know more about our offerings, please write to info@ltimindtree.com.
References:
https://aws.amazon.com/compliance/nist/
Latest Blogs
Core banking platforms like Temenos Transact, FIS® Systematics, Fiserv DNA, Thought Machine,…
We are at a turning point for healthcare. The complexity of healthcare systems, strict regulations,…
Clinical trials evaluate the efficacy and safety of a new drug before it comes into the market.…
Introduction In the upstream oil and gas industry, drilling each well is a high-cost, high-risk…




