CXOs Aim to Seize Quantum Communication Power with Early Investment
Quantum communication has emerged as a new frontier for data security, and companies are racing to get there first. This technology can make communication far more efficient than it currently is. It can protect information against hacking measures by sending multiple copies of messages through different quantum channels.
Quantum communication will revolutionize how we send and receive data, which comes at a critical time. By ensuring secure communication uniquely and providing tracking and tracing of information through immutable proof of where they are stored, distributed quantum computing can take place. In turn, this has benefits for the future of the world economy.
However, noise limits quantum communication capacity. Hence there are many restrictions on our ability to utilize quantum communication channels fully. These restrictions limit quantum communication devices’ storage and processing capabilities.
IT leaders have been understandably wary of investing in quantum technologies. However, this is beginning to change, and they have started constructing basic quantum communication networks. Within these networks, quantum states are produced at specific sources before being conveyed over a quantum channel to the receiver, which measures the received quantum states. These networks will emerge as an alternative solution to ensure secure information transfer and will open new avenues for realizing high-performance communication networks.
Aside from developing prepare-and-measure quantum communication networks, CXOs are focusing on devising mechanisms capable of implementing secure key distribution, certified random number generation, and entanglement swapping. They are targeting infrastructure, hardware components, security, and software platforms. Once their innovations mature, CIOs and their teams will use sophisticated approaches such as quantum artificial intelligence and quantum cloud to maximize the new service delivery.
Corporations, universities, and governments have embarked on the research bandwagon of the quantum channel’s ‘golden phase’ through funding and collaboration. Various analysts have cited cumulative government investments of up to ~USD 23 billion. A significant amount of seed funding is also being diverted to infrastructure and hardware development that would make such mechanisms of quantum communication safe, reliable, affordable, and practical.
At this stage of development, the collaboration will help everyone quickly take quantum communication solutions to the market. Furthermore, enterprises are better positioned for faster growth owing to early partnership opportunities and emerging go-to-market channels.
We believe that the realization of quantum communication will lead to the creation of a quantum internet, revolutionizing multipartite information transfer and sharing. This is likely to herald the use of other quantum technologies, such as distributed quantum computing, in the second quantum revolution.
Why Do You Need a Quantum Communication solution?
The world generates around 2.5 quintillion bytes of data per day. Organizations cannot estimate how much of this information is secure. They are struggling to find how vulnerable their data is on the web. Over the last decade, cybersecurity has emerged as a danger to commodity businesses and markets, with hackers attempting to steal data and disrupt the flow of resources.
As per the CPR research, globally, the average weekly number of attacks per organization exceeded 1,130 in 2022. The healthcare sector witnessed the most significant spike in average weekly attacks, with a 60% YoY increase in 2022. According to Energy Security Sentinel, 13 cybersecurity incidents targeting energy infrastructure took place in 2022, the most in a single year since 2016. Last year, a ransomware assault by hackers on the world’s single largest petroleum exporter in Saudi Arabia resulted in a data breach and an effort to extort $50 million from the state-controlled oil firm.
One of the most severe cyber-attacks occurred earlier this year when malware attacked loading facilities in Germany and extended to major terminals on the Amsterdam-Rotterdam-Antwerp network. There were 17 terminals affected (11 in Germany and 6 in the Amsterdam-Rotterdam-Antwerp hub).
As these instances increase, there is a need for a robust defense strategy that goes beyond traditional communication boundaries and offers impregnable security. In this situation, quantum communication can protect the data with security layers impermeable to phishing and other cyber-attacks.
In quantum communication, a qubit represents numerous states. The data packet is attached with these qubit-based encryption keys, thus encrypting the data across multiple states. The recipient is then supplied the data packet plus the encryption key, and it is possible to tell if the key is the same for both parties using a process called key sifting. Decrypting such a data packet without a verified decryption key is extremely difficult. Thus, transmitting quantum data packets results in highly secure data transfer. The decryption of a data packet containing many qubits can take years. Several laboratory studies and satellite-based communication have already demonstrated its efficacy.
Building upon this, quantum communication will enable the creation of a quantum internet where the global exchange of information can be done quickly, with better security protocols and robust and strong cryptography. Since cryptography encompasses most use cases relating to messaging, transmission, token security, quantum safe key generation, and other security features, there will be a global need for quantum cryptography.
LTIMindtree Crystal – Quantum Communication RADAR
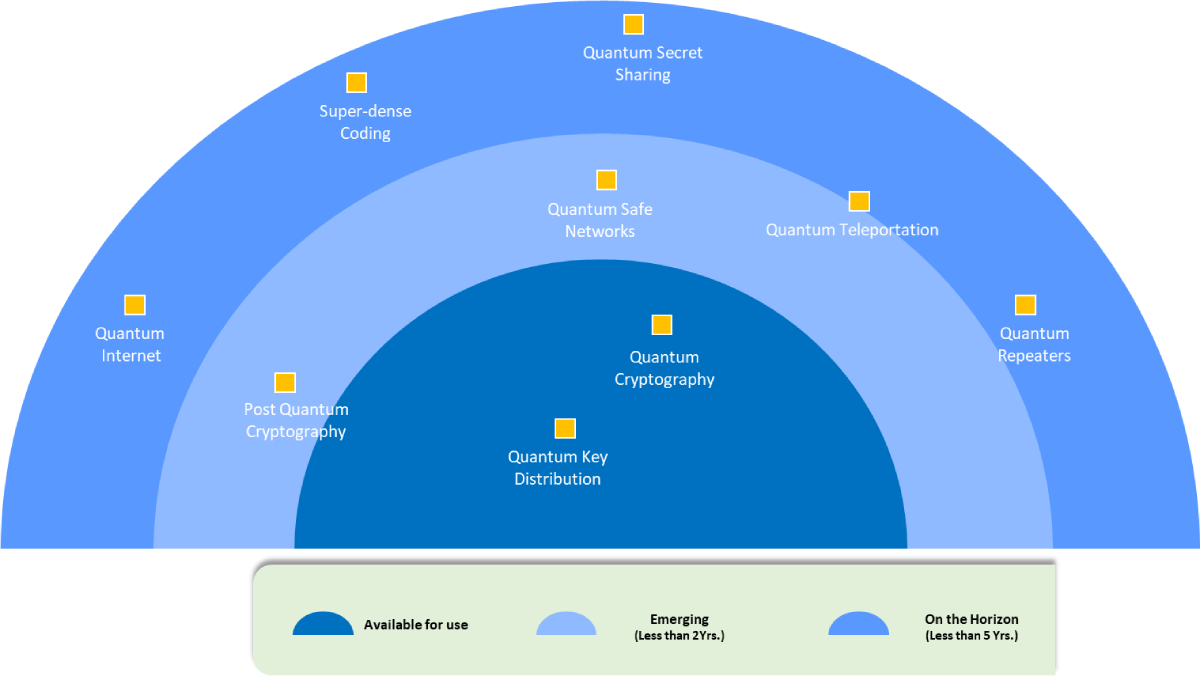
Fig.1: LTIMindtree Crystal – Quantum Communication RADAR
How can enterprises achieve better ROI by leveraging quantum communication?
Quantum communication’s ROI, particularly quantum cryptography, is difficult to determine. Quantum cryptography has several benefits that are difficult to translate into an immediate monetary advantage. However, considering quantum cryptography ROI is necessary in order to make a business decision. To better understand the ROI for quantum cryptography, we take a hypothetical analysis below. In this example, we are looking to prevent direct financial loss due to data breaches using quantum cryptography.
First, we will calculate Annual Loss Expectancy (ALE): an expected [approximate] financial loss caused by risks and threats (if not properly mitigated).
ALE = (Number of Incidents per Year) X (Potential Loss per Incident)
- Number of Incidents per Year: 12 [ one serious intrusion attempt per month]
Average cost per breach
- Cost of customer database and other sensitive information theft and exposure: USD 20,000
- Cost of banking portal unavailability during forensics and recovery: USD 15,000
- Cost of third-party experts allocated to investigate and remediate the breach: USD 10,000
- Cost of legal and compliance fines: USD 5000
Potential loss per incident = (Cost of customer database and other sensitive information theft and exposure) + (Cost of banking portal unavailability during forensics and recovery) + (Cost of third-party experts allocated to investigate and remediate the breach) + (Cost of legal and compliance fines)
Potential Loss per Incident = 20,000+15,000+10,000+5,000
Potential Loss per Incident = USD 50,000
Thus,
ALE = (Number of Incidents per Year) X (Potential Loss per Incident)
ALE = 12 X USD 50,000
ALE = USD 600,000
This is the amount a company is expected to lose per year using current data security protocols. Of course, each new incident will aggravate the losses.
Quantum cryptography solution will provide a better protection layer against bots and other malicious “noise,” automated attacks, and script-kiddies and continuously provide vulnerability scanning and security monitoring solution.
The average cost of setting up a quantum cryptographic system: USD 150,000
Thus, ROI will be,
ROI = (ALE / Cost of Countermeasures) X 100%
ROI = ($600,000 / $150,000) X 100%
ROI = 400%
How to Get Started in Quantum Communication?
While quantum communication technology and quantum-safe cryptography are still incubating, organizations should begin identifying their most crucial and sensitive data today to ensure a secure transition later. Organizations should keep track of government websites such as the NIST and the US Department of Homeland Security to stay updated on the latest quantum security standards.
We believe the following steps could be taken by different enterprises preparing for quantum communication technology to reach the mainstream.
- Quantum communication has a very high potential to become the de facto standard for all encrypted messaging and security requirements dependent on tokens, keys, and certificates, even if it is still a few years away from gaining general usage. Businesses must develop the necessary skill sets in advance to reduce security vulnerabilities brought on by ever-improving computing capabilities. CXOs must identify how to leverage assets created by their partners and have these assets in ready-to-deploy mode.
- The initial steps towards standardization of quantum-resistant cryptographic algorithms have already been taken by NIST, approving four such algorithms – 3 for digital signatures and 1 for general encryption. Apart from standardization, adopting these would significantly improve the security of our digital assets.
- Keeping up with the updates in this domain through industry forums, identifying areas or use cases vulnerable to a potential security breach, and leveraging on assets produced by the think-tank and organizations in this space would help with targeted solutions being implemented at a faster rate.
- While academia is adept in technology incubation, helping the industry to implement such innovations more efficiently. Industry can help with an efficient incubation process by identifying the appropriate solutions to solve the problems of tomorrow.
- Estimating the Cost of a potential Incident (CoPI) involving factors like direct costs, downtime costs, lawsuits, breach of regulatory requirements, privacy violations, and data leaks has still not been a focus area somehow. Prioritizing estimations on such costs as a part of standard processes can help with business cases for implementing quantum-safe communication.
Road Ahead
To fortify IT, business models, CXOs, and CISOs find potential leverage in Quantum Communication through its many possibilities in the realm of practical adoption of cybersecurity measures for securing, monitoring, tracking, and measuring high-value data in transit.
The transition from conventional communication to quantum communication will take time. For instance, the quantum communication hardware is yet to reach market maturity, or QKD system implementation may require an infrastructure overhaul that will make its adoption difficult.
Finally, even the most agile IT teams struggle with change. People who are used to working on RSA and AES algorithms may take some time to adjust to quantum algorithms. For enterprises that just started cultivating skill sets in advance and later forming a dedicated team to design and deploy quantum-proof algorithms to mitigate security threats may be beneficial.
Fortunately, some of the necessary quantum cryptographic protocols are easily available in the form of cloud-based solutions. The remainder can be accomplished in the next five years through engineering and a purposeful, constant emphasis on creating a Quantum future.
Delve into the world of Quantum Communication by visiting Solving-with-Quantum
More from Hakimuddin Bawangaonwala
In today's interconnected application ecosystem, data security and privacy are more significant…
This decade has been dominated by AI advancements. Generative AI took center stage in late…
A new generation of smart, intelligent, and interactive workspace technology has emerged over…
Introducing the future of AI - generative AI We are in the golden period of AI (Artificial…
Latest Blogs
Core banking platforms like Temenos Transact, FIS® Systematics, Fiserv DNA, Thought Machine,…
We are at a turning point for healthcare. The complexity of healthcare systems, strict regulations,…
Clinical trials evaluate the efficacy and safety of a new drug before it comes into the market.…
Introduction In the upstream oil and gas industry, drilling each well is a high-cost, high-risk…





