A Proactive Approach to Addressing the Risks in Enterprise Content Management (ECM) System
Content services security overview
Content services, known as content management services (CMS), refer to a set of technologies and processes. They are designed to create, organize, store, manage, and deliver digital content. The primary goal of content services is to streamline content creation and distribution across various platforms. It ensures that relevant and accurate information is accessible to the right audience at the right time.
These systems are traditionally called Enterprise Content Management Systems (ECM). The choice of whether to use “content services” or “ECM” in a specific context or reference often depends on the focus of the discussion. If the emphasis is on the newer, more agile approach to content management, “content services” may be preferred. Conversely, when talking about the broader and more traditional notion of content management within an enterprise setting, the term “ECM” can be employed.
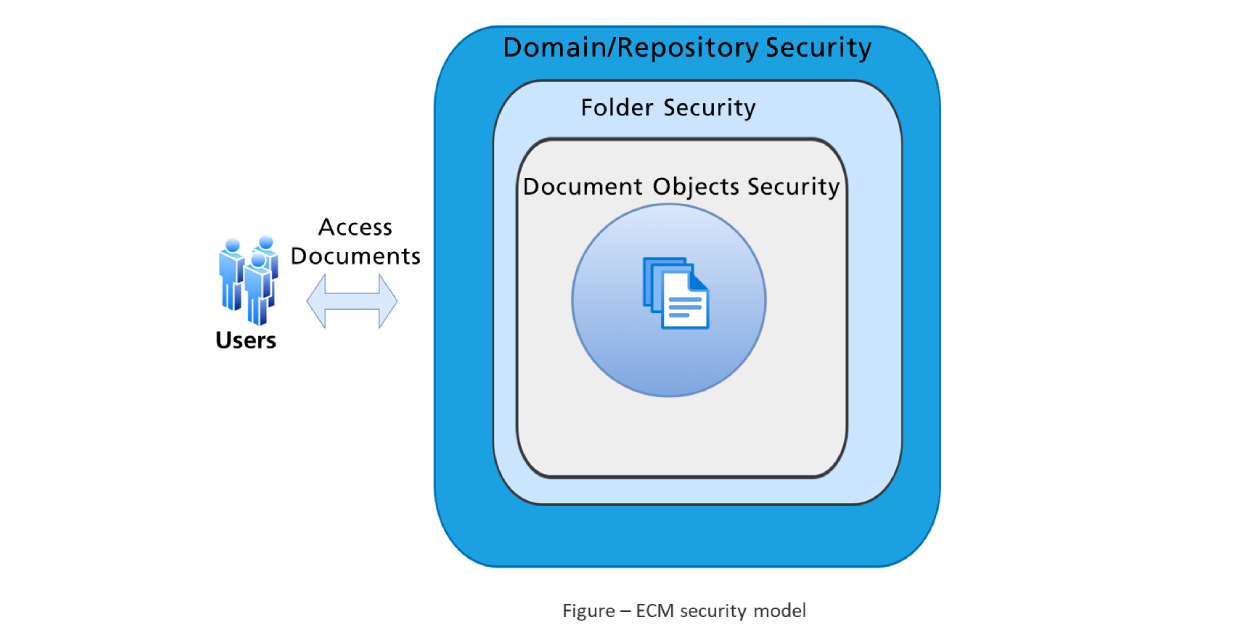
Document security is a key element of every project delivery in content services. A standard or generic approach to defining and implementing security enables users and applications to add content securely. This approach minimizes change overheads by allowing for controlled, extendable access. A codified method is implemented to define repositories and security groups, which allows for greater reuse and fewer revisions.
Organizations widely use enterprise content services to manage and organize their business content. However, as the amount of data stored in these ECM systems grows, so does the need for robust security measures. Failing to implement robust security measures in content services can expose enterprises to various risks. These risks include data breaches, legal consequences, loss of trust, and operational disruptions. Investing in strong security practices is crucial to safeguard sensitive information and maintain the integrity and reputation of the organization. This blog post will discuss the recommended methods to safeguard content services systems and ensure their protection.
For enterprises looking to implement content services security, it is important to consider the following approach:
1. Implement a security-first approach
A security-first approach involves designing and implementing security measures into your ECM system from the outset. To ensure security, the approach should encompass access control, data encryption, and consistent monitoring and auditing of the ECM system.
2. Secure user access
User access controls are crucial for safeguarding data confidentiality, integrity, and availability within an ECM system. They play a vital role in compliance, risk mitigation, and overall security posture, helping organizations prevent unauthorized access, data breaches, and other security incidents. To ensure that users can only access the content that is necessary for their job functions, controls must be put in place. Additionally, mechanisms such as multi-factor authentication and strong password policies should be used to prevent unauthorized access.
3. Use data encryption
It is recommended to encrypt all data whether in transit or at rest, using industry-standard encryption protocols like Secure Sockets Layer (SSL), Transport Layer Security (TLS), or Advanced Encryption Standard (AES).
4. Regularly update and patch the ECM system
Keeping the ECM system up-to-date with the latest security patches and updates is critical to maintaining a secure environment. Neglecting ECM security patches invites risks like vulnerabilities, breaches, and incompatibility. Many security vulnerabilities are discovered and addressed through software updates, so it is essential to stay up-to-date with the latest releases.
5. Periodically monitor and audit the ECM system
Regular monitoring and auditing of your ECM system can help identify potential security issues before they become major problems. This includes monitoring user activity and access logs to identify any unusual behaviour. It also includes performing routine security audits to identify vulnerabilities and take preventive measures to fix them.
6. Implement a disaster recovery plan
A disaster recovery plan is critical to ensure that the ECM system can recover quickly during a security breach or any other disaster. This plan should include regular backups of your content, as well as a strategy to restore the system in the event of a failure.
ECM best practices
When considering an ECM security solution, it is important to ensure that it includes:
- Encryption for stored data
- A strong authentication system
- Auditing capabilities
- Frequent updates to maintain stability and security
- Inheritance model
This model enables the determination of an object’s security based on its position in a containment hierarchy. Additionally, as in any subordinate relationship, it inherits its security from the same object. The placement of an object in a container does not automatically activate inheritance; it must be set by identifying the container as a security parent. In this case, the Access Control Lists (ACL) is then checked as part of this authorization process. This allows folders to have specific ACL settings that can supersede or augment security on objects that they contain.
- Marking sets model
Marking sets are intended to provide a mechanism to support records management of the content inside of FileNet. It allows specific metadata attributes to be identified that control the effective access of an object in conjunction with its ACL. Due to the specific design intentions of marking sets, this security mechanism is utilized if there is no other feature that can provide the model needed.
- Security policies model
This serves as a collection of security templates. These templates have pre-set Access Control Entries (ACEs) that can be customized to apply to a document, custom object, or folder. Unless stated otherwise, this topic explains how security policies are linked to documents and their classes. Security policies allow system administrators to apply access control to large numbers of documents without directly editing the ACL on each document.
Conclusion
In summary, securing an ECM system requires a combination of strong access controls, data encryption, and regular updates and patching. It also includes monitoring, auditing, and a disaster recovery plan. Setting up security is a big part of how the ECM systems works and meets project needs. Before the project commences or any documents are relocated, it is vital to ensure that everything is done accurately. It’s wise to invest time in the initial stages to ensure everything is done correctly and prepare for possible future alterations.
References:
- Security, IBM, February 9, 2023: https://www.ibm.com/docs/en/filenet-p8-platform/5.5.x?topic=development-security#sec_concepts__sec_security_policy_object
- Understanding security inheritance, IBM, March 5, 2021: https://www.ibm.com/docs/en/filenet-p8-platform/5.2.0?topic=authorization-understanding-security-inheritance
- What are Content Services Platforms?, Gartner Peer Insights: https://www.gartner.com/reviews/market/content-services-platforms
Latest Blogs
Introduction What if training powerful AI models didn’t have to be slow, expensive, or data-hungry?…
Pharmaceutical marketing has evolved significantly with digital platforms, but strict regulations…
Leveraging the right cloud technology with appropriate strategies can lead to significant cost…
Introduction The financial industry drives the global economy, but its exposure to risks has…